IT security in all phases of software development
Fixing a security problem in existing software is many times more expensive than identifying and avoiding it at the planning stage. In a Secure Software Development Lifecycle (Secure SDLC), information security is included right from the start and in all phases of development: This makes it possible to reconcile agile development and IT security while saving costs and effort.
DevOps tools for automating security checks help to keep the manual workload to a minimum. In addition to product and code security, we also safeguard against other threats and examine your software supply chains (software supply chain security), for example.
Our goal is to help your organization transform, provide you with a framework for secure software development, and create awareness of information security – so you and your developers emerge from the project with renewed confidence and expertise in information security.
Considering the multiple dimensions of information security in all phases and areas can quickly become overwhelming: That’s why we are happy to support you in integrating information security into your SDLC and help you create the appropriate processes. This way you can develop secure software faster and more reliably.
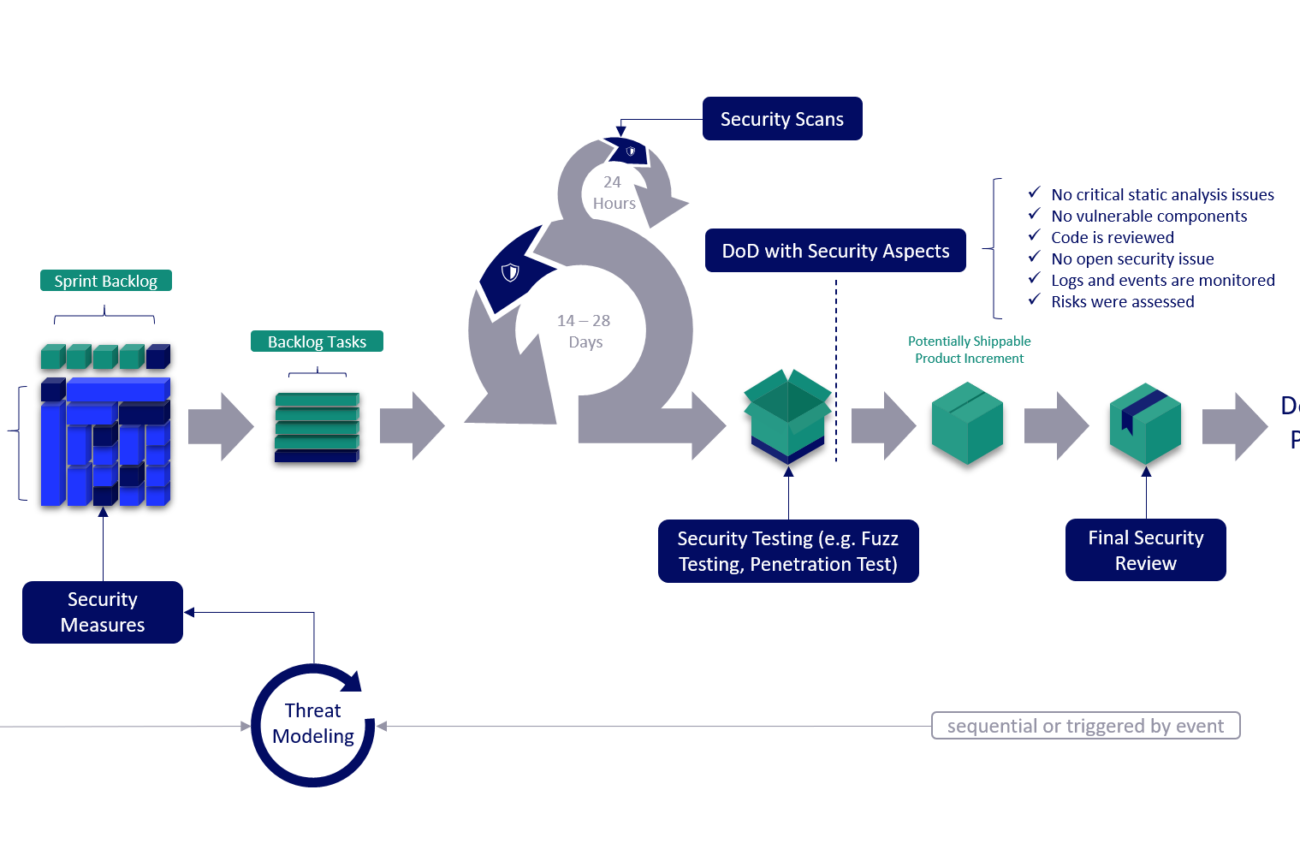
Phases of the SSDLC
Our methodology is based on Microsoft's Security Development Lifecycle and includes the following phases, which should be cycled through at 1-2 year intervals:
Training
To implement a successful Secure SDLC, it is essential that all employees develop an awareness of information security. Therefore, during the training phase, an awareness workshop tailored to your company is held to raise awareness of information security, as well as a workshop on secure software development.
Requirements
In order to evaluate the security level and maturity of the software in the following steps, we evaluate here which security requirements are relevant for you and create Quality Gates & Bug Bars.
Design
Through threat modeling, we model attack scenarios and the attack surface of your products to create a threat profile that helps you prioritize the right measures to secure them. This takes the form of collaborative threat modeling workshops, in which our security experts work with your team to evaluate and improve the architecture in terms of information security. Here we are guided by industry standards such as STRIDE or Abuse Cases.
Implementation
With the use of SAST tools (Static Application Security Testing, also known as static code analysis), security-critical bugs are detected before they enter your codebase. We help you integrate these tools into your development workflow using CI/CD pipelines so that your developers can focus on developing new features.
Verification
Once a new iteration of a product has been completed, its security requirements are evaluated prior to release and it is ensured that the product is adequately secured. Using fuzz testing and a penetration test, we uncover security vulnerabilities and simulate attacks on the product. In this phase, a final security review is performed and finally the product is released.
Release
Before the final release, an incident response plan must be created. This provides instructions for minimizing damage and thwarting further attacks in the event of a security incident, and ensures that you are well prepared for attacks in the event of an emergency. Vulnerability management ensures that you can inform your customers quickly and efficiently in the event that security vulnerabilities are discovered.
Contact us today
We advise you in a non-binding conversation
Frequently Asked Questions (FAQ):
Can Agile project management such as Scrum or Kanban be reconciled with an SSDLC?
Yes – our Secure Software Development Lifecycle is aligned with modern development methodologies such as Scrum and supports Agile processes by incorporating information security at various stages without compromising team productivity.
What does the Secure Software Development Training Workshop include?
Depending on the product your company develops, we will discuss typical vulnerabilities, demonstrate their causes and illustrate the corresponding solutions. For example, if you develop web applications, we will be guided by the OWASP Top 10, if you develop system software in C++, we will discuss typical programming problems such as memory errors, race conditions or unsafe macros, according to Mitre CWE.
Furthermore, we show the use of tools that help developers to test their code for security vulnerabilities, such as fuzzers, DAST (Dynamic Application Security Testing) or IAST (Interactive Security Testing) tools.
An introduction to information security concepts such as the SSDLC itself, CVEs or CVSS scoring as well as an excursus on the secure use of cryptography round off the presentation.
Each workshop is therefore individually tailored to your company.
Are security tools for automating audits expensive? Can we also use open source solutions?
OTARIS is a vendor-independent consultant – we do not force an expensive commercial solution on you, but advise you according to your needs and recommend tools that fit your business. Most commercial tools have free open source alternatives, which are more than sufficient for small to medium sized businesses.
Can I perform a penetration test myself?
The advantage of an external tester over an internal developer, besides the expertise in offensive security, is the external perspective on your product – uncovering edge cases that would otherwise often not even be considered. More about our pentest methodology can be found here.
Architectural Risk Analysis / Threat Modeling also benefits from the same principle.
How can software supply chain attacks be prevented?
The first step towards a secure software supply chain is to become aware of the (transitive) dependencies in your own software. Often, many third-party libraries are used, which in turn have further dependencies. If a security gap occurs here, yourown product may also be affected.
To enable an automated check, we recommend the use of Software Bills of Materials (SBOMs) and/or a Software Composition Analysis (SCA) tool. These make it possible to scan project dependencies on a regular basis and to immediately detect security vulnerabilities caused by external dependencies.
We already have a mature software product, can we also implement an SSDLC afterwards?
Yes, you can. Often, long-standing software has security deficiencies in its architecture and development workflow, and therefore also benefits from a Secure SDLC.

